Cryptocurrencies have turn into a everlasting fixture within the international monetary panorama. Crypto near-instant settlements by way of blockchain expertise has revolutionized funds and worth trade in ways in which had been solely imaginations prior to now. Nevertheless, this innovation has come at a price.
Malicious actors are more and more concentrating on crypto tasks and platforms to capitalize on the recognition and worth of cryptocurrencies and exploit their vulnerabilities for private acquire. Additionally, they’re deploying refined ways, generally mixed, to inflict most injury on their victims.
In 2022, the Axie Infinity mission reportedly misplaced billions of {dollars} in the Ronin Bridge assault, which was perpetuated by way of a phishing assault on the mission’s workers. Extra just lately, attackers breached Ethereum co-founder Vitalik Buterin’s X (previously Twitter) account by way of a sim swap assault and promoted a false NFT. Victims suffered losses exceeding $691,000.
Crypto exchanges, which function central transaction factors, usually are not not noted; actually, they’re hotspots for assaults and profitable targets for hackers. Just lately, HTX (previously Huobi) was hacked, ensuing within the theft of roughly $30 million price of cryptocurrencies from its trade pockets, following an analogous incident with Poloniex, which suffered a hack draining over $100 million in several cryptocurrencies.
This evolution of crypto hacks has highlighted the pressing want for improved safety measures on this dynamic and fast-paced atmosphere. Nevertheless, to implement enough safety measures, it’s essential to grasp the motives behind these actions.
Crypto Hacks Below the Microscope
Whereas there have been cases of “white hat” hackers who intention to spur safety fixes by exposing vulnerabilities, most crypto hacks and thefts goal private acquire. For instance, in November 2023, when Kyberswap, a DEX aggregator, fell sufferer to exploitation throughout a number of blockchains, ensuing within the theft of $46 million, the hacker demanded full govt management over the mission as a situation for returning the stolen funds. As of December 5, the case is ongoing, and the hacker is dissatisfied with the provided 10% of the $47 million and isn’t content material with the financial compensation alone.
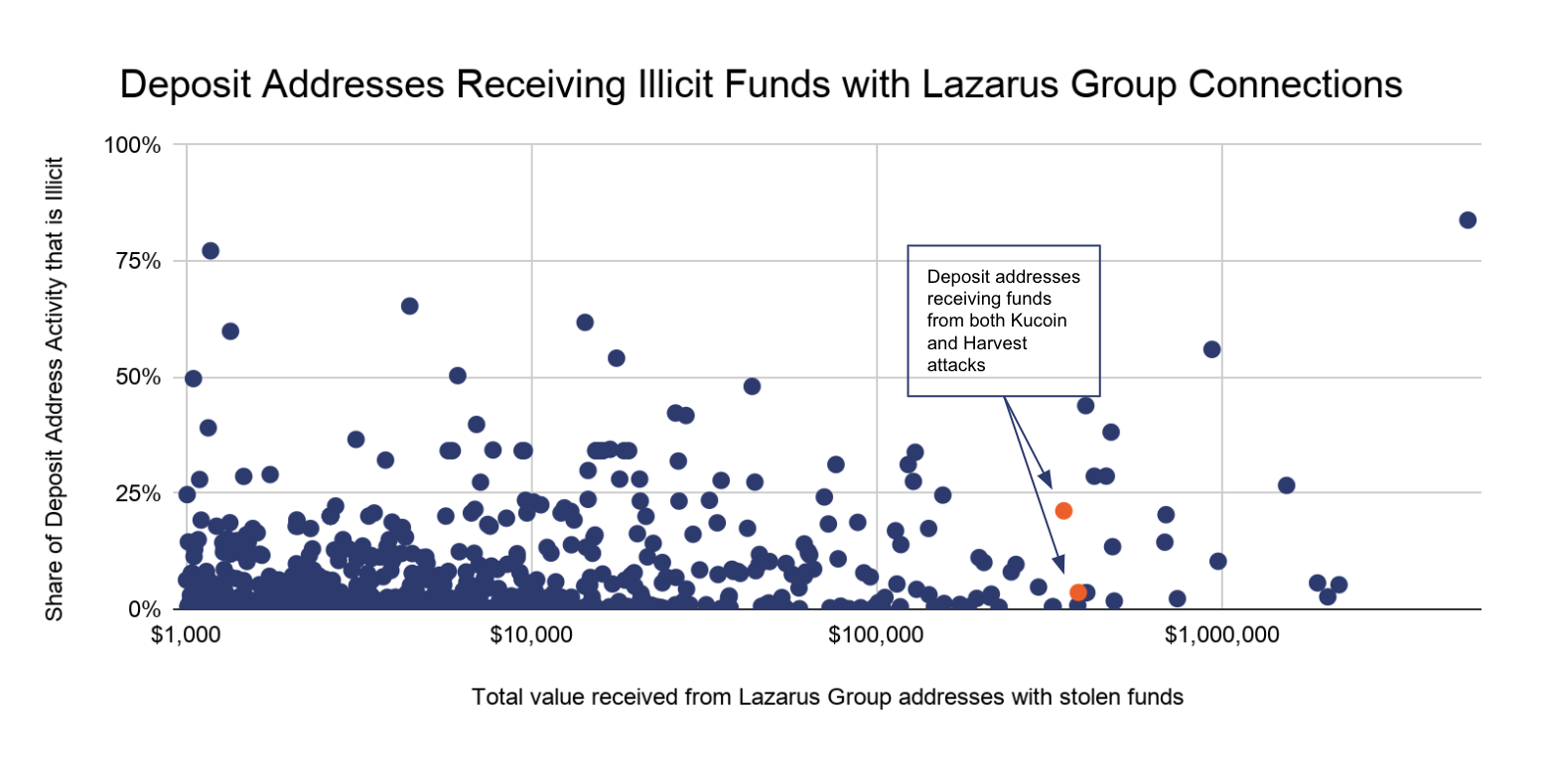
Crypto hacks might also contain state pursuits. The Lazarus group is believed to have stolen roughly $3 billion in crypto property over the previous six years, with round $1.7 billion stolen in 2022 alone. The 2023 Crypto Crime Report by Chainalysis reveals that $1.1 billion of this sum resulted from DeFi protocol hacks. The group’s reference to North Korean authorities highlights the opportunity of state-sponsored backing for crypto hacks.
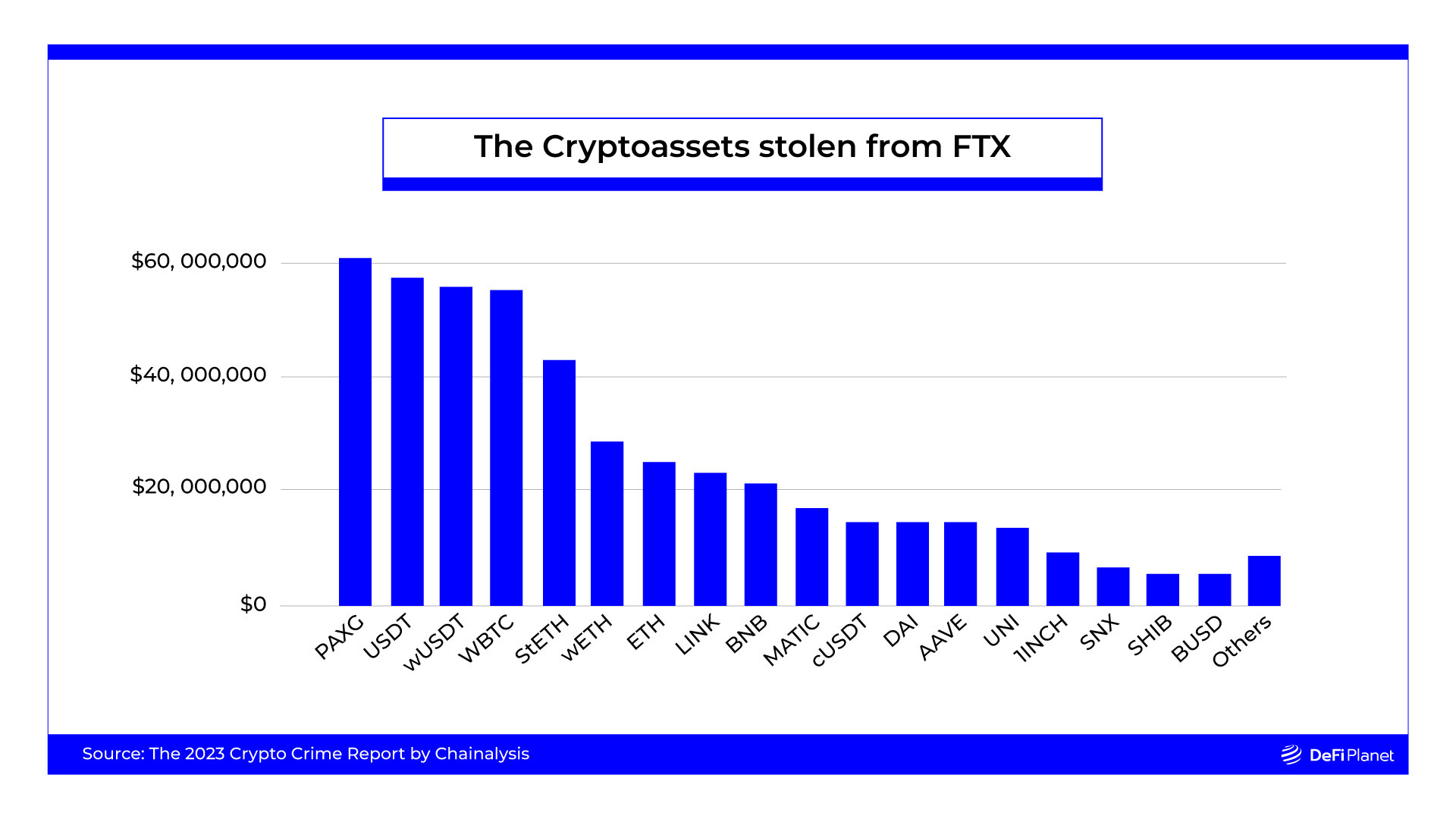
Lastly, FTX was hacked on the day it filed for chapter, November 12, 2022, dropping about $420 million. The breach was triggered by a swift switch of the now-bankrupt trade’s property to varied storage sorts following its chapter declaration. Whereas the precise motive stays unknown, there are suspicions of insider liquidation. Apparently, regardless of the numerous loss, this explicit hack didn’t obtain enough consideration, possibly as a result of robust backlash surrounding FTX’s enterprise fundamentals.
To summarize, there are numerous motives behind crypto hacks, starting from private acquire to state and insider pursuits. Understanding this enables for a greater conception of the vulnerabilities within the cryptocurrency panorama and the work required to enhance the person and builder expertise on this area.
How Can We Mitigate This Rising Danger
Cryptocurrency platforms and tasks are accountable for guaranteeing their main product/platform code is meticulously designed and safety is prioritized in all codes and programs. In an trade that values the ethos of ‘ship quick and break issues,’ builders should acknowledge that swift deployment carries the danger of considerable losses if issues go awry. Subsequently, underscoring cautious design and establishing with safety in thoughts is crucial for establishing a resilient system that safeguards person funds.
Though code audits by entities like Hacken, OpenZeppelin, and PeckShield are commonplace within the crypto house, they haven’t utterly thwarted malicious actions attributable to their remedy as one-time endeavours. Crypto companies should acknowledge the persistent efforts of hackers and may constantly interact respected third-party audit companies to make sure ongoing scrutiny. Plus, the outcomes of those audits ought to be shared with the neighborhood to reveal points and their resolutions.
Along with partaking third-party programs for scrutiny, tasks ought to implement programs actively monitoring transactions for anomalies and suspicious actions, doubtlessly automating responses to cut back reliance on human intervention. Early detection of unusually giant transactions or a number of transactions to the identical tackle in a brief interval serves as an preliminary signal of an assault. Automating responses primarily based on such occasions can expedite the mitigation course of, limiting potential injury in hours or minutes reasonably than days or even weeks.
Past monitoring for potential assaults, it’s also important to have a response plan in place. To create a response system, mission builders must map out attainable methods an assault may happen and methods to react in such eventualities. Whereas this isn’t a fail-safe technique, it does the mission on some stage of preparedness helps to get well quicker within the case of a breach. Swift responses, even within the occasion of fund losses, are important for stopping additional losses and constructing belief within the protocol’s group.
On one other word, customers are additionally accountable for safeguarding their investments. Crypto is supposed to be decentralized; thus, utilizing these centralized platforms comes with an enormous threat that the customers should abide by, regardless that they might be profitable for actions like lending and staking. The very best recommendation for crypto customers is to make use of non-custodial wallets and chilly storage choices. Although it means their property are totally of their care, it minimises the avenues by way of which attackers can entry crypto investments.
A crypto investor should additionally pay attention to the ways utilized by scammers and the newest developments of their assaults. Understanding how phishing, malware, and clicking on random hyperlinks can lead to funding losses may also help make knowledgeable selections when confronted with such conditions.
Whereas there’s no common answer, a mixture of recurring audits, lively safety and operational monitoring, automated incident response programs, and person proactiveness can considerably mitigate this rising threat of asset loss by way of crypto hacks. Trade-wide adoption of those measures can relegate most of those widespread safety incidents to tales of the previous.
Closing Ideas
Given the decentralized nature of crypto companies, the trade requires a proactive, real-time safety strategy. Strong safety choices and operational monitoring of system inter-relationships and the community state are important for fostering belief and inspiring extra individuals to undertake the expertise.
Extra than simply the technological tweaking, a widespread security-first mindset also can act as a deterrent for attackers, as they know that quick detection awaits them. This type of community-led safety monitoring efforts incentivizes vigilance and supplies transparency into protocol operational well being, guaranteeing general ecosystem safety.
Disclaimer: This piece is meant solely for informational functions and shouldn’t be thought of buying and selling or funding recommendation. Nothing herein ought to be construed as monetary, authorized, or tax recommendation. Buying and selling or investing in cryptocurrencies carries a substantial threat of economic loss. All the time conduct due diligence.
If you wish to learn extra information articles like this, go to DeFi Planet and comply with us on Twitter, LinkedIn, Fb, Instagram, and CoinMarketCap Group.